Bon c’est officiel, il semblerait que mon Facture.exe laborieusement dépacké dans un précédent article (Hash 17832c9a78b36c8a3133e2c2e24ebc3b9896763a chez Malware.lu, version dépackée hash 13d0f11c18170923fa88005309a9ec16 ) Soit en fait un bon vieux malware Zeus. Et voici pourquoi ;
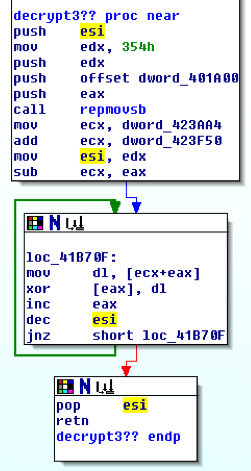
Quand on le regarde un peu sous toutes ses coutures, on se rend compte que 2 fonctions sont souvent appelées Ces fonctions sont des déobfuscateurs de string, car en plus d’être packé ce malware contient des strings obfusquée (décidémment il ne veulent pas qu’on voye ce qu’il font ).
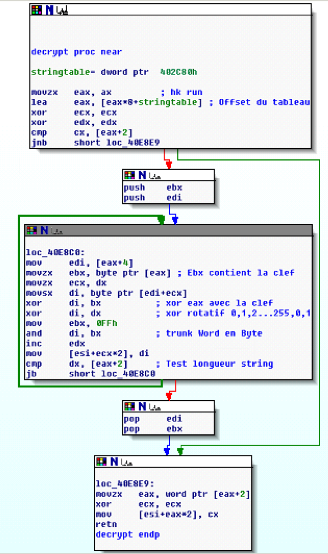
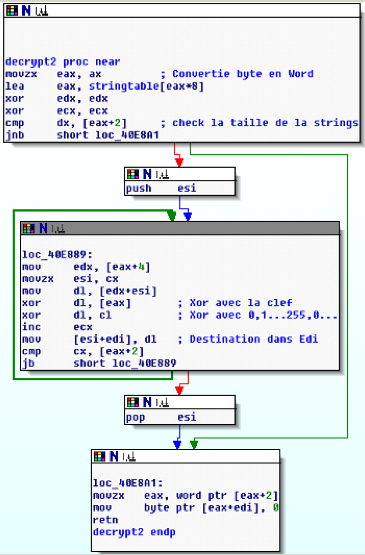
La première fonction est à l’offset 0x0040E8AA, c’est un double xor. On l’appelle en mettant dans EAX l’offset de la string voulue du grand tableau d’encodage, et le résultat est une string décodée posé a l’emplacement de EDI.
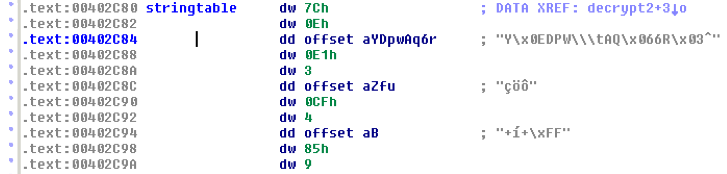
Le tableau a le format suivant ;
- 1 Word : Clef d’encodage du Xor de cette string
- 1 Word : Longueur de la string
- 1 DWord : Addresse de la chaine encodée
Il est posé à l’offset 0x00402C7E
Et bien sur les strings sont des belles stringZ xorées avec leur 0 à la fin ;)
J’ai donc pondu un petit script pour sortir d’un coup toutes ces strings, je l’ai mis dans mon Git de Tools à Chall (Après tout c’est juste un chall à 0 points)
$ ./dcod_zeustr.py
Str:00 Len:000e Key:007c Off:0040499c %s://%s:%s@%s/
Str:01 Len:0003 Key:00e1 Off:00404998 ftp
Str:02 Len:0004 Key:00cf Off:00404990 pop3
Str:03 Len:0009 Key:0085 Off:00404984 anonymous
Str:04 Len:001d Key:002a Off:00404964 grabbed\%S_%02u_%02u_%02u.txt
Str:05 Len:0019 Key:00c0 Off:00404948 Grabbed data from: %s
%S
Str:06 Len:0030 Key:00dd Off:00404914 %s%s
Referer: %S
User input: %s
%sPOST data:
%S
Str:07 Len:0007 Key:0005 Off:0040490c *EMPTY*
Str:08 Len:0009 Key:0021 Off:00404900 *UNKNOWN*
Str:09 Len:000a Key:00a6 Off:004048f4 *BLOCKED*
Str:0a Len:0012 Key:00d8 Off:004048e0 Content-Type: %s
Str:0b Len:000a Key:0077 Off:004048d4 ZCID: %S
Str:0c Len:0021 Key:00a5 Off:004048b0 application/x-www-form-urlencoded
Str:0d Len:0032 Key:001b Off:0040487c HTTP authentication: username="%s", password="%s"
Str:0e Len:0022 Key:0052 Off:00404858 HTTP authentication (encoded): %S
Str:0f Len:000f Key:00cd Off:00404848 Mozilla\Firefox
Str:10 Len:0007 Key:00e1 Off:00404840 user.js
Str:11 Len:000c Key:0095 Off:00404830 profiles.ini
Str:12 Len:0009 Key:00e2 Off:00404824 Profile%u
Str:13 Len:000a Key:009b Off:00404818 IsRelative
Str:14 Len:0004 Key:0096 Off:00404810 Path
Str:15 Len:0146 Key:00d0 Off:004046c8 user_pref("network.cookie.cookieBehavior", 0);
user_pref("privacy.clearOnShutdown.cookies", false);
user_pref("security.warn_viewing_mixed", false);
user_pref("security.warn_viewing_mixed.show_once", false);
user_pref("security.warn_submit_insecure", false);
user_pref("security.warn_submit_insecure.show_once", false);
Str:16 Len:0055 Key:0085 Off:00404670 user_pref("browser.startup.homepage", "%s");
user_pref("browser.startup.page", 1);
Str:17 Len:0029 Key:005b Off:00404644 Software\Microsoft\Internet Explorer\Main
Str:18 Len:000a Key:0032 Off:00404638 Start Page
Str:19 Len:0033 Key:001b Off:00404604 Software\Microsoft\Internet Explorer\PhishingFilter
Str:1a Len:0007 Key:0022 Off:004045fc Enabled
Str:1b Len:0009 Key:0037 Off:004045f0 EnabledV8
Str:1c Len:002c Key:007e Off:004045c0 Software\Microsoft\Internet Explorer\Privacy
Str:1d Len:000c Key:00ab Off:004045b0 CleanCookies
Str:1e Len:0044 Key:0069 Off:00404568 Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\%u
Str:1f Len:0004 Key:006c Off:00404560 1406
Str:20 Len:0004 Key:0043 Off:00404558 1609
Str:21 Len:001b Key:00c2 Off:0040453c Accept-Encoding: identity
Str:22 Len:0005 Key:000c Off:00404534 TE:
Str:23 Len:0014 Key:0059 Off:0040451c If-Modified-Since:
Str:24 Len:000a Key:0053 Off:00404510
Path: %s
Str:25 Len:0006 Key:0036 Off:00404508 %s=%s
Str:26 Len:0007 Key:0017 Off:00404500 *@*.txt
Str:27 Len:0003 Key:00d4 Off:004044fc Low
Str:28 Len:0026 Key:009c Off:004044d4 Wininet(Internet Explorer) cookies:
%S
Str:29 Len:0005 Key:0057 Off:004044cc Empty
Str:2a Len:0017 Key:0097 Off:004044b4 Macromedia\Flash Player
Str:2b Len:000f Key:0081 Off:004044a4 flashplayer.cab
Str:2c Len:0005 Key:0056 Off:0040449c *.sol
Str:2d Len:0014 Key:006a Off:00404484 Windows Address Book
Str:2e Len:001e Key:0058 Off:00404464 SOFTWARE\Microsoft\WAB\DLLPath
Str:2f Len:0007 Key:006f Off:0040445c WABOpen
Str:30 Len:0010 Key:007e Off:00404448 Windows Contacts
Str:31 Len:0006 Key:00f2 Off:00404440 A8000A
Str:32 Len:0003 Key:007c Off:0040443c 1.0
Str:33 Len:002f Key:0036 Off:0040440c EmailAddressCollection/EmailAddress[%u]/Address
Str:34 Len:0017 Key:000e Off:004043f4 Windows Mail Recipients
Str:35 Len:001a Key:002d Off:004043d8 Outlook Express Recipients
Str:36 Len:000f Key:00e7 Off:004043c8 Outlook Express
Str:37 Len:0014 Key:00e5 Off:004043b0 account{*}.oeaccount
Str:38 Len:001f Key:006e Off:00404390 Software\Microsoft\Windows Mail
Str:39 Len:0024 Key:00fd Off:00404368 Software\Microsoft\Windows Live Mail
Str:3a Len:000a Key:007f Off:0040435c Store Root
Str:3b Len:0004 Key:00fb Off:00404354 Salt
Str:3c Len:0004 Key:00a9 Off:0040434c 0x%s
Str:3d Len:000c Key:00df Off:0040433c Windows Mail
Str:3e Len:0011 Key:0055 Off:00404328 Windows Live Mail
Str:3f Len:000e Key:00a6 Off:00404318 MessageAccount
Str:40 Len:000c Key:00e1 Off:00404308 Account_Name
Str:41 Len:0012 Key:0040 Off:004042f4 SMTP_Email_Address
Str:42 Len:001e Key:00c1 Off:004042d4 %sAccount name: %s
E-mail: %s
Str:43 Len:0031 Key:001a Off:004042a0 %s:
Server: %s:%u%s
Username: %s
Password: %s
Str:44 Len:0009 Key:00b7 Off:00404294 %s_Server
Str:45 Len:000c Key:001b Off:00404284 %s_User_Name
Str:46 Len:000c Key:00fc Off:00404274 %s_Password2
Str:47 Len:0007 Key:0031 Off:0040426c %s_Port
Str:48 Len:0014 Key:0061 Off:00404254 %s_Secure_Connection
Str:49 Len:0004 Key:000b Off:0040424c SMTP
Str:4a Len:0004 Key:0015 Off:00404244 POP3
Str:4b Len:0004 Key:00be Off:0040423c IMAP
Str:4c Len:0006 Key:000a Off:00404234 (SSL)
Str:4d Len:0012 Key:00b7 Off:00404220 ftp://%s:%s@%s:%u
Str:4e Len:000f Key:00c6 Off:00404210 ftp://%s:%s@%s
Str:4f Len:0012 Key:008a Off:004041fc ftp://%S:%S@%S:%u
Str:50 Len:001c Key:0064 Off:004041dc yA36zA48dEhfrvghGRg57h5UlDv3
Str:51 Len:0009 Key:009f Off:004041d0 sites.dat
Str:52 Len:0009 Key:0080 Off:004041c4 quick.dat
Str:53 Len:000b Key:0064 Off:004041b8 history.dat
Str:54 Len:0002 Key:0085 Off:004041b4 IP
Str:55 Len:0004 Key:007c Off:004041ac port
Str:56 Len:0004 Key:0088 Off:004041a4 user
Str:57 Len:0004 Key:006a Off:0040419c pass
Str:58 Len:0013 Key:00ef Off:00404188 SOFTWARE\FlashFXP\3
Str:59 Len:000a Key:001f Off:0040417c datafolder
Str:5a Len:000a Key:004b Off:00404170 *flashfxp*
Str:5b Len:0008 Key:003b Off:00404164 FlashFXP
Str:5c Len:000b Key:00f9 Off:00404158 wcx_ftp.ini
Str:5d Len:000b Key:0039 Off:0040414c connections
Str:5e Len:0007 Key:001d Off:00404144 default
Str:5f Len:0004 Key:00ad Off:0040413c host
Str:60 Len:0008 Key:00ea Off:00404130 username
Str:61 Len:0008 Key:009e Off:00404124 password
Str:62 Len:0020 Key:00dd Off:00404100 SOFTWARE\Ghisler\Total Commander
Str:63 Len:000a Key:0072 Off:004040f4 ftpininame
Str:64 Len:000a Key:0046 Off:004040e8 installdir
Str:65 Len:000a Key:0096 Off:004040dc *totalcmd*
Str:66 Len:0011 Key:00af Off:004040c8 *total*commander*
Str:67 Len:0009 Key:00e3 Off:004040bc *ghisler*
Str:68 Len:000f Key:0089 Off:004040ac Total Commander
Str:69 Len:000a Key:0006 Off:004040a0 ws_ftp.ini
Str:6a Len:0008 Key:00ab Off:00404094 _config_
Str:6b Len:0004 Key:007d Off:0040408c HOST
Str:6c Len:0004 Key:0053 Off:00404084 PORT
Str:6d Len:0003 Key:0039 Off:00404080 UID
Str:6e Len:0003 Key:007f Off:0040407c PWD
Str:6f Len:0018 Key:005a Off:00404060 SOFTWARE\ipswitch\ws_ftp
Str:70 Len:0007 Key:0023 Off:00404058 datadir
Str:71 Len:000a Key:00d5 Off:0040404c *ipswitch*
Str:72 Len:0006 Key:008b Off:00404044 WS_FTP
Str:73 Len:0005 Key:0060 Off:0040403c *.xml
Str:74 Len:000b Key:0056 Off:00404030 /*/*/Server
Str:75 Len:0004 Key:00a8 Off:00404028 Host
Str:76 Len:0004 Key:003a Off:00404020 Port
Str:77 Len:0004 Key:00d1 Off:00404018 User
Str:78 Len:0004 Key:0048 Off:00404010 Pass
Str:79 Len:000b Key:0095 Off:00404004 *filezilla*
Str:7a Len:0009 Key:0060 Off:00403ff8 FileZilla
Str:7b Len:001e Key:00d2 Off:00403fd8 SOFTWARE\Far\Plugins\ftp\hosts
Str:7c Len:001f Key:002c Off:00403fb8 SOFTWARE\Far2\Plugins\ftp\hosts
Str:7d Len:0008 Key:0023 Off:00403fac hostname
Str:7e Len:0008 Key:006d Off:00403fa0 username
Str:7f Len:0004 Key:0026 Off:00403f98 user
Str:80 Len:0008 Key:00ec Off:00403f8c password
Str:81 Len:000b Key:00ac Off:00403f80 FAR manager
Str:82 Len:0029 Key:0039 Off:00403f54 SOFTWARE\martin prikryl\winscp 2\sessions
Str:83 Len:0008 Key:00b0 Off:00403f48 hostname
Str:84 Len:000a Key:0007 Off:00403f3c portnumber
Str:85 Len:0008 Key:003a Off:00403f30 username
Str:86 Len:0008 Key:0022 Off:00403f24 password
Str:87 Len:0006 Key:004b Off:00403f1c WinSCP
Str:88 Len:000b Key:003c Off:00403f10 ftplist.txt
Str:89 Len:0008 Key:0039 Off:00403f04 ;server=
Str:8a Len:0006 Key:0065 Off:00403efc ;port=
Str:8b Len:0006 Key:00d6 Off:00403ef4 ;user=
Str:8c Len:000a Key:00d3 Off:00403ee8 ;password=
Str:8d Len:000e Key:0014 Off:00403ed8 ftp*commander*
Str:8e Len:000d Key:0066 Off:00403ec8 FTP Commander
Str:8f Len:001e Key:00dd Off:00403ea8 SOFTWARE\ftpware\coreftp\sites
Str:90 Len:0004 Key:0076 Off:00403ea0 host
Str:91 Len:0004 Key:0066 Off:00403e98 port
Str:92 Len:0004 Key:00dd Off:00403e90 user
Str:93 Len:0002 Key:0016 Off:00403e8c pw
Str:94 Len:0007 Key:007f Off:00403e84 CoreFTP
Str:95 Len:0005 Key:006f Off:00403e7c *.xml
Str:96 Len:000c Key:0032 Off:00403e6c FavoriteItem
Str:97 Len:0004 Key:000d Off:00403e64 Host
Str:98 Len:0004 Key:002a Off:00403e5c Port
Str:99 Len:0004 Key:00b1 Off:00403e54 User
Str:9a Len:0008 Key:00df Off:00403e48 Password
Str:9b Len:0037 Key:0051 Off:00403e10 SOFTWARE\smartftp\client 2.0\settings\general\favorites
Str:9c Len:0012 Key:0031 Off:00403dfc personal favorites
Str:9d Len:002c Key:0013 Off:00403dcc SOFTWARE\smartftp\client 2.0\settings\backup
Str:9e Len:0006 Key:00e5 Off:00403dc4 folder
Str:9f Len:0008 Key:000e Off:00403db8 SmartFTP
Str:a0 Len:000c Key:0035 Off:00403da8 userinit.exe
Str:a1 Len:0004 Key:004f Off:00403da0 pass
Str:a2 Len:001e Key:00fd Off:00403d80 certs\%s\%s_%02u_%02u_%04u.pfx
Str:a3 Len:0007 Key:00f3 Off:00403d78 grabbed
Str:a4 Len:000b Key:00d7 Off:00403d6c os_shutdown
Str:a5 Len:0009 Key:002a Off:00403d60 os_reboot
Str:a6 Len:000d Key:0052 Off:00403d50 bot_uninstall
Str:a7 Len:000a Key:0045 Off:00403d44 bot_update
Str:a8 Len:000e Key:00b7 Off:00403d34 bot_update_exe
Str:a9 Len:000a Key:00bc Off:00403d28 bot_bc_add
Str:aa Len:000d Key:0016 Off:00403d18 bot_bc_remove
Str:ab Len:0016 Key:0006 Off:00403d00 bot_httpinject_disable
Str:ac Len:0015 Key:009d Off:00403ce8 bot_httpinject_enable
Str:ad Len:000b Key:00e3 Off:00403cdc fs_path_get
Str:ae Len:000d Key:0043 Off:00403ccc fs_search_add
Str:af Len:0010 Key:002a Off:00403cb8 fs_search_remove
Str:b0 Len:000c Key:0017 Off:00403ca8 user_destroy
Str:b1 Len:000b Key:0062 Off:00403c9c user_logoff
Str:b2 Len:000c Key:002e Off:00403c8c user_execute
Str:b3 Len:0010 Key:00e4 Off:00403c78 user_cookies_get
Str:b4 Len:0013 Key:001c Off:00403c64 user_cookies_remove
Str:b5 Len:000e Key:00c4 Off:00403c54 user_certs_get
Str:b6 Len:0011 Key:0026 Off:00403c40 user_certs_remove
Str:b7 Len:000e Key:006d Off:00403c30 user_url_block
Str:b8 Len:0010 Key:008d Off:00403c1c user_url_unblock
Str:b9 Len:0011 Key:00ef Off:00403c08 user_homepage_set
Str:ba Len:0013 Key:0060 Off:00403bf4 user_ftpclients_get
Str:bb Len:0015 Key:0044 Off:00403bdc user_emailclients_get
Str:bc Len:0014 Key:00ea Off:00403bc4 user_flashplayer_get
Str:bd Len:0017 Key:003d Off:00403bac user_flashplayer_remove
Str:be Len:0012 Key:007e Off:00403b98 Not enough memory.
Str:bf Len:0018 Key:00ce Off:00403b7c Script already executed.
Str:c0 Len:0023 Key:006a Off:00403b58 Failed to load local configuration.
Str:c1 Len:0023 Key:00c0 Off:00403b34 Failed to save local configuration.
Str:c2 Len:0025 Key:00df Off:00403b0c Failed to execute command at line %u.
Str:c3 Len:001b Key:00d6 Off:00403af0 Unknown command at line %u.
Str:c4 Len:0003 Key:0070 Off:00403aec OK.
Str:c5 Len:0007 Key:000b Off:00403ae4 Winsta0
Str:c6 Len:0007 Key:00cc Off:00403adc default
Str:c7 Len:001c Key:000d Off:00403abc screenshots\%s\%04x_%08x.jpg
Str:c8 Len:0007 Key:00a2 Off:00403ab4 unknown
Str:c9 Len:000a Key:002a Off:00403aa8 image/jpeg
Str:ca Len:002d Key:00e9 Off:00403a78 Software\Microsoft\Windows\Currentversion\Run
Str:cb Len:003b Key:00bb Off:00403a3c SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\%s
Str:cc Len:0010 Key:00a2 Off:00403a28 ProfileImagePath
Str:cd Len:000f Key:00de Off:00403a18 unknown\unknown
Str:ce Len:004c Key:00db Off:004039c8 :d
rd /S /Q "%s"
rd /S /Q "%s"
if exist "%s" goto d
if exist "%s" goto d
Str:cf Len:0007 Key:00b9 Off:004039c0 dwm.exe
Str:d0 Len:000c Key:0063 Off:004039b0 taskhost.exe
Str:d1 Len:000b Key:006d Off:004039a4 taskeng.exe
Str:d2 Len:000b Key:00c1 Off:00403998 wscntfy.exe
Str:d3 Len:000a Key:0002 Off:0040398c ctfmon.exe
Str:d4 Len:000b Key:0032 Off:00403980 rdpclip.exe
Str:d5 Len:000c Key:009a Off:00403970 explorer.exe
Str:d6 Len:0017 Key:00f8 Off:00403958 V %08X
C %08X
PS %08X
Str:d7 Len:0010 Key:0007 Off:00403944 BOT NOT CRYPTED!
Str:d8 Len:0029 Key:0001 Off:00403918 SOFTWARE\Microsoft\Windows\CurrentVersion
Str:d9 Len:000b Key:00b9 Off:0040390c InstallTime
Str:da Len:0010 Key:006b Off:004038f8 WindowsProductId
Str:db Len:000b Key:00e3 Off:004038ec %s_%08X%08X
Str:dc Len:000b Key:00df Off:004038e0 fatal_error
Str:dd Len:0007 Key:00b7 Off:004038d8 unknown
Str:de Len:0074 Key:0059 Off:00403860 SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
Str:df Len:0072 Key:00be Off:004037e8 SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\DomainProfile\AuthorizedApplications\List
Str:e0 Len:0015 Key:005d Off:004037d0 %windir%\explorer.exe
Str:e1 Len:0030 Key:00a1 Off:0040379c %windir%\explorer.exe:*:Enabled:Windows Explorer
Str:e2 Len:0053 Key:00b7 Off:00403748 netsh advfirewall firewall add rule name="explore" dir=in action=allow program="%s"
Str:e3 Len:000c Key:00e4 Off:00403734 wtsapi32.dll
Str:e4 Len:0015 Key:00e2 Off:0040371c WTSEnumerateSessionsW
Str:e5 Len:000d Key:000e Off:0040370c WTSFreeMemory
Str:e6 Len:0011 Key:0032 Off:004036f8 WTSQueryUserToken
Str:e7 Len:000b Key:0028 Off:004036ec userenv.dll
Str:e8 Len:001f Key:002e Off:004036cc GetDefaultUserProfileDirectoryW
Str:e9 Len:000a Key:0011 Off:004036c0 user32.dll
Str:ea Len:000b Key:004c Off:004036b4 MessageBoxW
Str:eb Len:0009 Key:008e Off:004036a8 ntdll.dll
Tout un programme n’est-ce pas !! La seconde fonction de décodage est disponible la l’offset 0x0040E874 et fait la même chose (Le mystêre reste entier, pourquoi 2 fonctions ??)
On retrouve dans ces strings des chaines de controle du botnet plus qu’explicite que google hésite à identifier comme Zeus 2.0 ou Citadel :
Str:a6 Len:000d Key:0052 Off:00403d50 bot_uninstall Str:a7 Len:000a Key:0045 Off:00403d44 bot_update Str:a8 Len:000e Key:00b7 Off:00403d34 bot_update_exe Str:a9 Len:000a Key:00bc Off:00403d28 bot_bc_add Str:aa Len:000d Key:0016 Off:00403d18 bot_bc_remove Str:ab Len:0016 Key:0006 Off:00403d00 bot_httpinject_disable Str:ac Len:0015 Key:009d Off:00403ce8 bot_httpinject_enable Str:b0 Len:000c Key:0017 Off:00403ca8 user_destroy Str:b1 Len:000b Key:0062 Off:00403c9c user_logoff Str:b2 Len:000c Key:002e Off:00403c8c user_execute Str:b3 Len:0010 Key:00e4 Off:00403c78 user_cookies_get Str:b4 Len:0013 Key:001c Off:00403c64 user_cookies_remove Str:b5 Len:000e Key:00c4 Off:00403c54 user_certs_get Str:b6 Len:0011 Key:0026 Off:00403c40 user_certs_remove Str:b7 Len:000e Key:006d Off:00403c30 user_url_block Str:b8 Len:0010 Key:008d Off:00403c1c user_url_unblock Str:b9 Len:0011 Key:00ef Off:00403c08 user_homepage_set Str:ba Len:0013 Key:0060 Off:00403bf4 user_ftpclients_get Str:bb Len:0015 Key:0044 Off:00403bdc user_emailclients_get Str:bc Len:0014 Key:00ea Off:00403bc4 user_flashplayer_get Str:bd Len:0017 Key:003d Off:00403bac user_flashplayer_remove
Quels sont les fonctionnalitées du notre ;
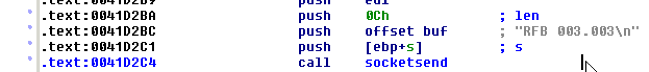
A l’offset 0x0041D2BA on retrouve un envoit sur un socket de la string RFB 003.003 ca sent le VNC Serveur ( RFB pour le protocole Remote Frame Buffer )
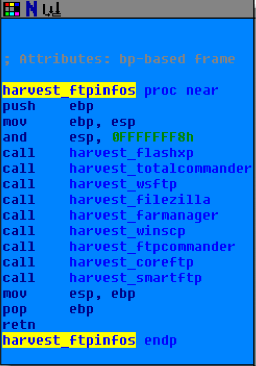
En décodant toutes les string et analysant un peut le code, on se rend compte que le malware est capable d’aller farfouiller dans bon nombre de fichier/base de registre de configuration de softs clients FTP à la recherche de crédentials. Le point d’entrée de ce moissonnage en masse est 0x00412B05
Autre truc Funky.. Manifestement il se permettra d’ouvrir le firewall.
$ ./decode.py | egrep netsh Str:e2 Len:0053 Key:00b7 Off:00403748 netsh advfirewall firewall add rule name="explore" dir=in action=allow program="%s"
Et j’en passe, Il s’approche de près des certificats, émettra des requêtes http. Bref c’est la fête et je suis loin d’avoir tout regardé et compris, il reste encore quelques fonction d’offuscation qui gardent encore leur mystère (voir 0x0041B6ED).
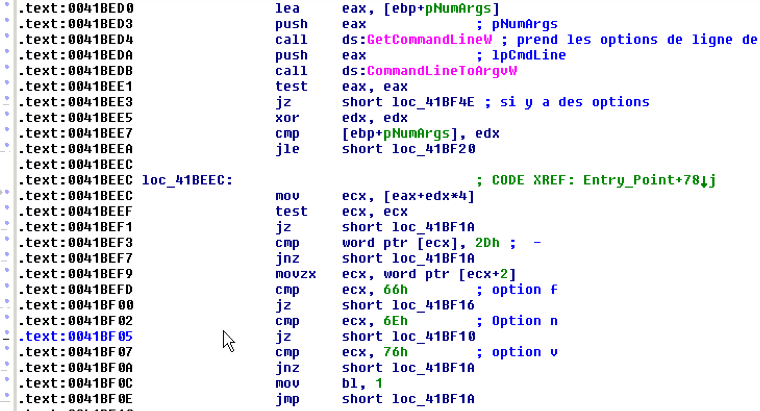
Alors, Zeus v2 ou Citadel, c’est la fonction qui parse les options de la ligne de commande qui m’a convaincu du Zeus. Dans notre code l’executable peut être lancé avec les options “f” “n” ou “v”
On peut trouver grace à google des ersatz de sources de Zeus qui semblent confirmer cela, Et encore j’ai pas la fonction “info” moi:
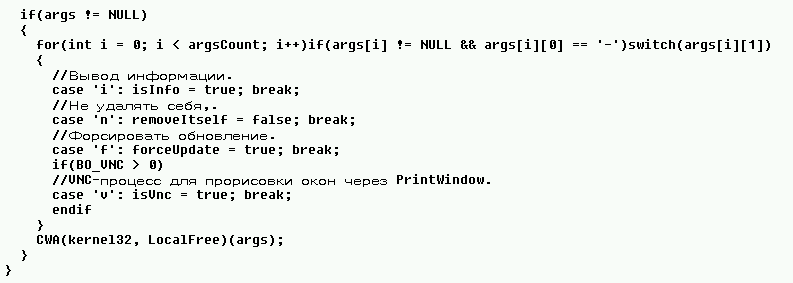 Mais quoi qu’il en soit, je suis loin d’avoir les options d’un Citatel si on en croit le blog de Hexacorn.
Mais quoi qu’il en soit, je suis loin d’avoir les options d’un Citatel si on en croit le blog de Hexacorn.
C’est donc un Zeus v2. Et c’est là qu’on se rend compte aussi de la qualité de la classification des malware par les antivirus (Quand c’est détecté) ;) Il faut les comprendre, avec ce qui doit sortir tous les jours c’est de l’abattage.
Antivirus Résultat Mise à jour Agnitum - 20121126 AhnLab-V2 Trojan/Win32.Zbot 20121126 AntiVir TR/Rogue.kdv.796538.1 20121127 Antiy-AVg - 20121127 Avast Win32:Malware-gen 20121127 AVG - 20121127 BitDefender Trojan.Generic.KDV.796538 20121127 ByteHero - 20121116 CAT-QuickHeal - 20121127 ClamAV - 20121127 Commtouch - 20121127 Comodo TrojWare.Win32.Trojan.Agent.Gen 20121126 DrWeb Trojan.Winlock.7431 20121127 Emsisoft Trojan.Win32.Zbot (A) 20121127 eSafe - 20121126 ESET-NOD32 a variant of Win32/Injector.ZMJ 20121126 F-Prot - 20121127 F-Secure Trojan.Generic.KDV.796538 20121127 Fortinet W32/Zbot.AQW!tr.pws 20121127 GData Trojan.Generic.KDV.796538 20121127 Ikarus Trojan.Win32.Inject 20121127 Jiangmin - 20121127 K7AntiVirus - 20121126 Kaspersky Trojan.Win32.Inject.ewuu 20121127 Kingsoft - 20121119 McAfee PWS-Zbot.gen.aqw 20121127 McAfee-GW-Ed PWS-Zbot.gen.aqw 20121126 Microsoft PWS:Win32/Zbot 20121127 MicroWorld-eScan Trojan.Generic.KDV.796538 20121127 Norman W32/Ransom.CNY 20121127 nProtect Trojan.Generic.KDV.796538 20121127 Panda Trj/CI.A 20121126 PCTools - 20121127 Rising - 20121126 Sophos Mal/EncPk-AFN 20121127 SUPERAntiSpyware - 20121127 Symantec - 20121127 TheHacker - 20121126 TotalDefense - 20121126 TrendMicro - 20121127 TrendMicro-HCall TROJ_GEN.F4AHZKQ 20121127 VBA32 - 20121124 VIPRE Trojan.Win32.Generic!BT 20121127 ViRobot Trojan.Win32.A.Inject.176000 20121127
Bon je vous quitte je vient de recevoir un mail de HSBC me demandant d’ouvrir un message sécurisé en .zip ;)


Pingback: A+ sous l’bus Google – Partie 2 | Blogcopter
Yep juste que l’antivirus, quand un ukrainien commence une campagne de botisation… Bin y trouvera rien ! tout ce travail pour rien ! La preuve, le facture.exe est passé via un Amavis tout bien configuré et à jour.
La seule prévention, c’est encore de bloquer de base tout ce qui peut s’exécuter.
http://www.mail-archive.com/amavis-user@lists.sourceforge.net/msg08199.html